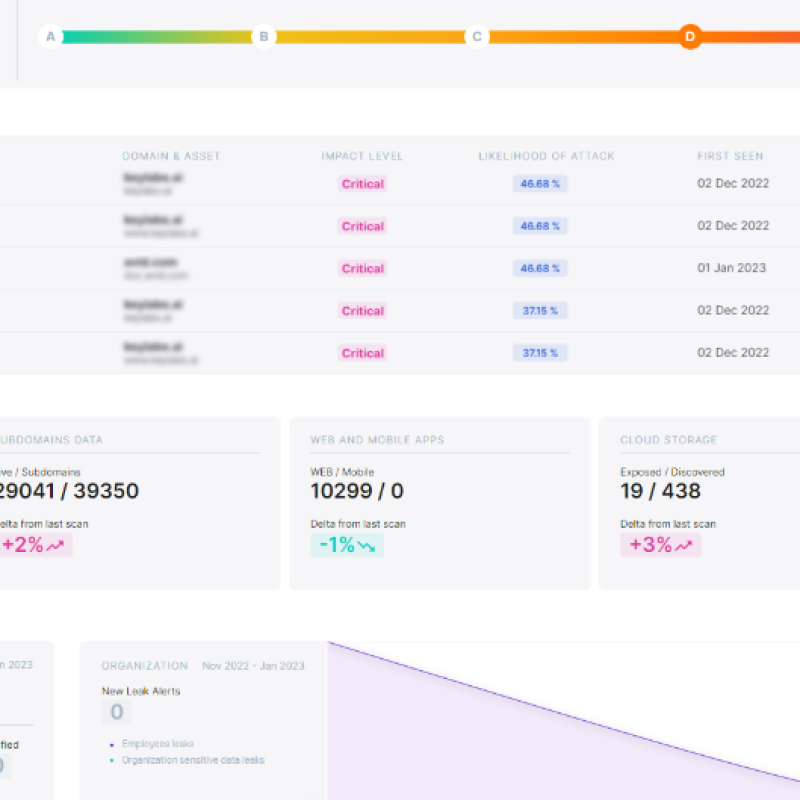
Understanding Your External Attack Surface
To predict where cybercriminals might strike, it’s crucial to understand how they see your company’s external attack surface. With business changes, cloud migration, and shadow IT, this surface is constantly evolving. These variations, often overlooked in annual assessments, present opportunities for cybercriminals looking to bypass your defenses. We provide the context and information you need to reduce your external risk. Utilize our unique perspective to prioritize findings, patch vulnerabilities, remediate misconfigured systems, and disconnect outdated or out-of-service assets. Our system continuously updates from various intelligence sources with the latest information on vulnerabilities and threats
An ASM that works for You
Advanced asset discovery and continuous identification of all your exposed assets, through the most sophisticated discovery engines.
Manage your exposed assets using our Attack Surface Management (ASM) solution. We cover Infrastructure, Cloud Configuration, Leaked Credentials, Exposed Assets, and Data Leaks.
Prevent breaches. Use our automated mitigation engines or let our experts do it for you. We offer Validation, Prioritization, Compromise Assessment, and Dependency Check.
With the ASM management system, we guide you in mitigating weaknesses through supervised remediation, validation, and processes to reduce false positives, providing accurate results. This includes CVE – Patches, Threat Hunting, and Ticket Management.
Attack Surface Management is essential in protecting against and reducing the impact of various risks:
- Outdated and unrecognized IT assets, legacy and shadow IT.
- Errors and oversights by individuals, including susceptibility to phishing scams and potential data breaches
- Software vulnerabilities due to outdated versions.
- Risks associated with the use of unknown open-source software.
- Broad-scale cyber threats specific to your industry.
- Focused cyber-attacks aimed directly at your organization.
- Violations of intellectual property rights.
- IT systems acquired through mergers and acquisitions.
- Broad-scale cyber threats specific to your industry.
- IT assets managed by external vendors.
Contact Us
FIll out the form below and we will contact you as soon as possible

Offices
- Rio Lerma 90, Mexico City, MEXICO
- Zorrilla 78, Madrid, SPAIN
- Ha-Shlosha 98, Tel Aviv, ISRAEL